RWMC is a Windows PowerShell script written as a proof of concept to Retrieve Windows Credentials using only PowerShell and CDB command-line options (Windows Debuggers).
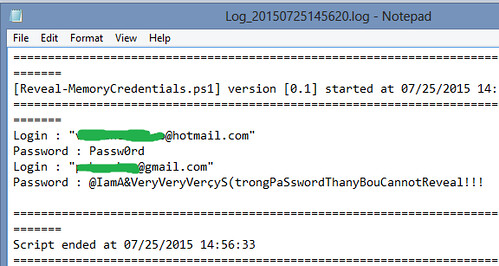
It allows to retrieve credentials from Windows 2003 to 2012 and Windows 10 (It was tested on 2003, 2008r2, 2012, 2012r2 and Windows 7 – 32 and 64 bits, Windows 8 and Windows 10 Home edition).
The script is different from Mimikatz or WCE because it doesn’t work with system .dlls to decrypt data. All the decryptions are made in the script.
Features
The main features of RWMC:
- Fully PowerShell
- Works locally, remotely or from a dump file collected on a machine
- Doesn’t use .dll files to locate credentials address in memory but a simple Microsoft debugger
- Doesn’t use OS .dll files to decipher passwords collected (AES, TripleDES, DES-X)
- Breaks undocumented Microsoft DES-X
- Works even if you are on a different architecture than the target
- Leaves no trace in memory
Requirements
To run this script effectively you need:
- PowerShell 3
- Allow PowerShell script on you machine, example : Set-ExecutionPolicy Unrestricted -force
- An Internet Connection
You can download RWMC here:
Or read more here.
The post RWMC – Retrieve Windows Credentials With PowerShell appeared first on Darknet - The Darkside.